Effectively security scan for Website
Watch the tutorial
step 1
Add domain and Verify
Add your domain or IP address of Web application, then verify your ownership.
step 2
Scan and Remediate
Create a scan profile and get started. When the results are available, you can proceed to fix the vulnerabilities.
Easily and quickly scan and fix website's security bugs
OWASP Top 10
Detect dangerous vulnerabilities of websites such as SQL injection, XSS, Broken Authentication and other known vulnerabilities.
Visual reporting
You will receive a detailed report for your websites, with important insights about the vulnerabilities and security level of your websites and IPs
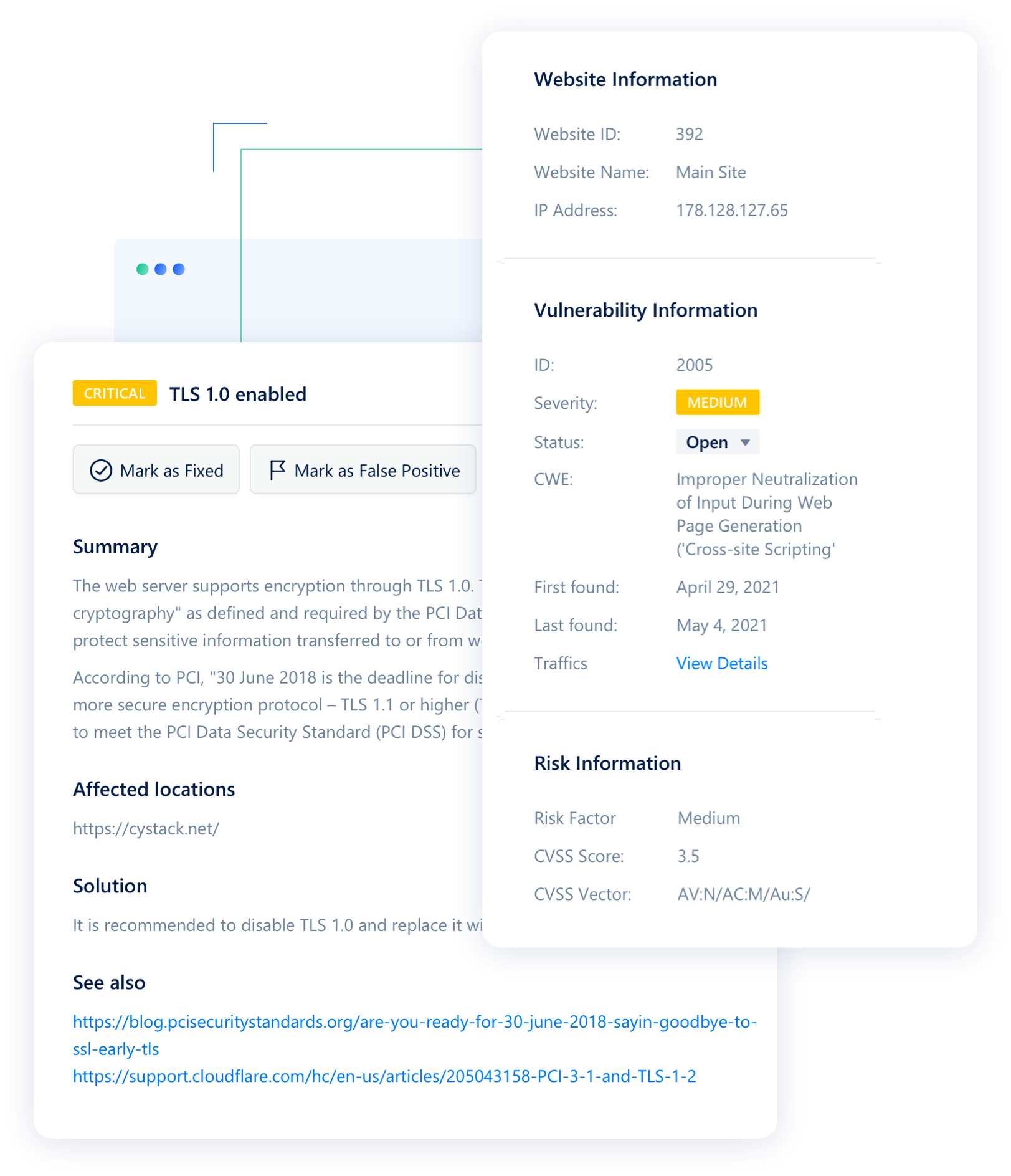
Vulnerability fixing
The detailed report includes the severity and location of the vulnerability, and suggested remediation methods to help you fix them easily
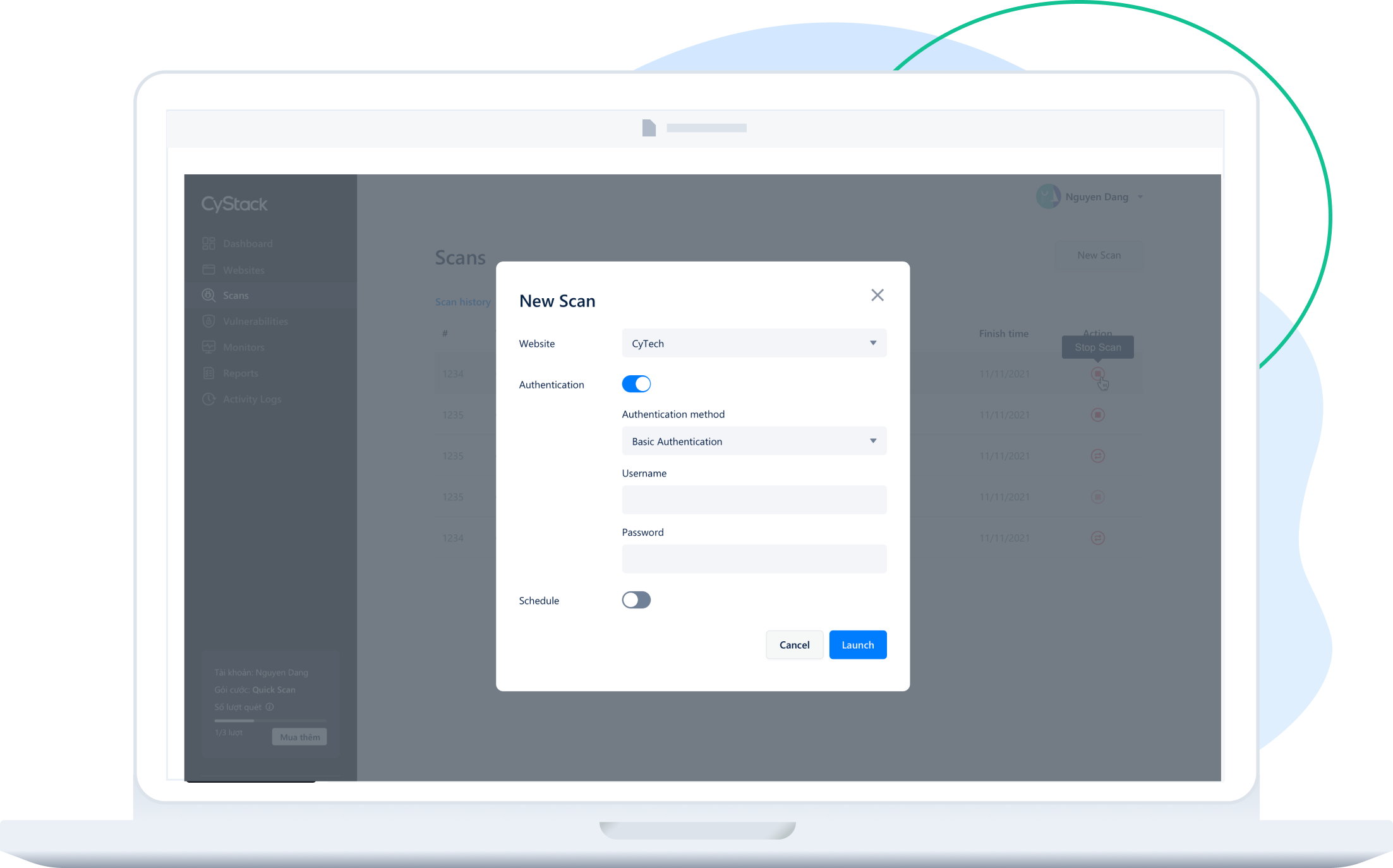
QUICK SCAN
Scan your website, your way
Scan for website vulnerabilities including OWASP Top 10 (SQLi, XSS, ...), configuration errors, known vulnerabilities (CVE). CWS protects your web applications from cyberattacks, important data disclosure or hijacking. You can conduct scans whenever you want at a reasonable cost per scan.
Detect most of the common vulnerabilities on the website.
Vulnerability data is updated regularly. Website will be more and more secure.
Allows schedule scans or recurring scans and scan websites with login feature.
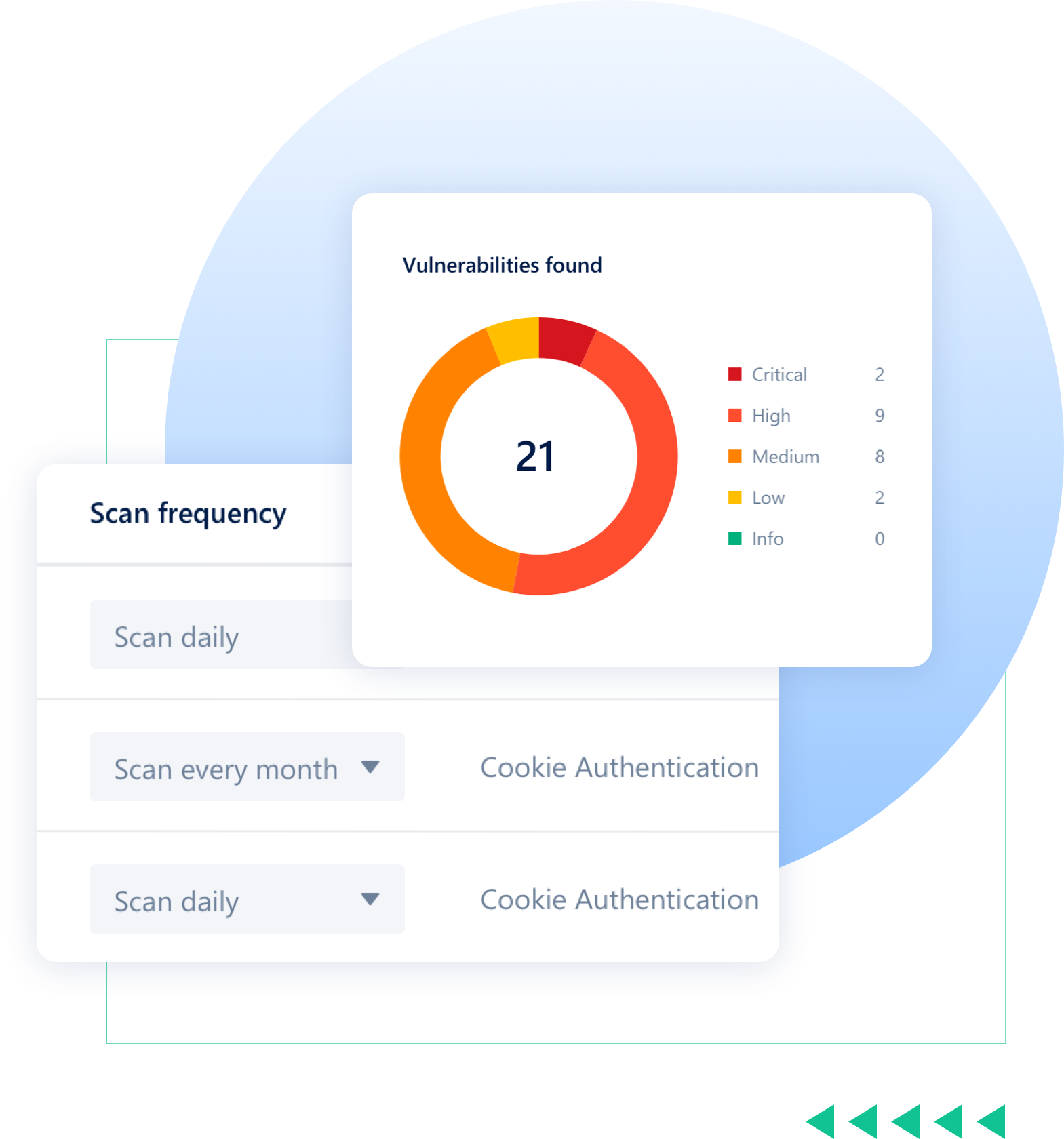
DEEP SCAN
Manage and address vulnerabilities at ease
With an intuitive dashboard and reporting interface, you can easily categorize the importance of each security flaw on your website, thereby having a panoramic view and a reasonable remediation plan. Deep Scan allows you to scan an unlimited number of scans in a month at a discounted price.
Scans websites, server IPs, APIs, and complex web applications, including sites that require login.
Classify and manage vulnerabilities according to the criteria of danger level, CVSS score, detection time, vulnerability position, etc. with filters.
View detailed information about the vulnerability such as its location, type, possible consequences, and remediation recommendations.
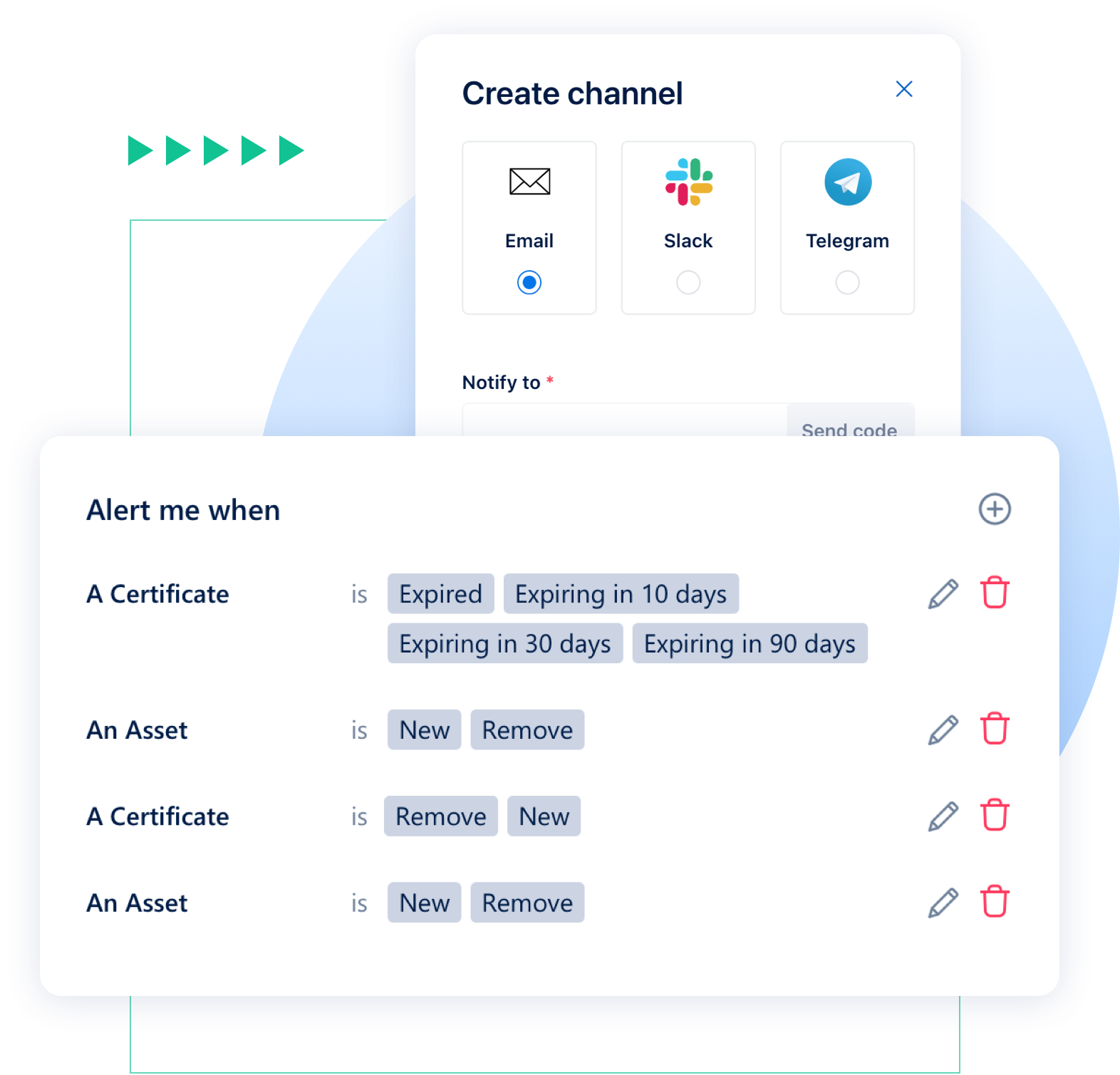
Integration
Custom notification system allows you to choose to receive reports of important information via Email, Slack, Telegram, Jira channels. Each team member can customize the message according to his or her job.
Get notified when a vulnerability is detected on a certain website.
Get notified when a vulnerability is fixed or when a scan is complete.
Get notified when a security certificate is about to expire.
Some dangerous vulnerabilities can affect your websites and applications

Broken Authentication
Authentication failure occurs when the website cannot authenticate the login session of the user or admin, which can let the attacker access the website without knowing the password

Misconfiguration
Security system misconfiguration can allow the attacker to gain access to parts or the whole system and perform harmful actions such as injecting malicious code, creating backdoors, stealing data, etc.

Injection
Vulnerabilities such as SQL injection can let your database be accessed by attackers and expose customer data.

Sensitive data leakage
No encryption, weak encryption or failure to manage keys, etc. can cause sensitive data to be leaked such as credit cards and user information

Known vulnerabilities - CVE
Using components that contain known vulnerabilities (CVE), your business will have a high risk of being attacked through these components. The consequences depend on how dangerous the vulnerabilities are.

Broken Access Control
Errors related to access permission occur in the absence of a continuous monitoring system. As a result, an attack can impersonate a user or an administrator. They can access, create, edit or delete files.

Insufficient Logging & Monitoring
Not keeping activity logs and not monitoring the system continuously are some of the leading causes of cyber attacks. In 2016, it took organizations or businesses an average of 161 days to discover a vulnerability in their system.

XSS
XSS (cross-site scripting) vulnerability allows attackers to capture user identifiers such as session tokens and cookies.
Protect your web application before hackers attack.

Quick Scan & Deep Scan
Scan entire websites and web applications for Injection, Broken Authentication, XSS, Misconfiguration, and other known vulnerabilities.
Get 1 free scan for each successful authenticated website.

Asset Monitoring
Monitor web apps and servers continuously, protect up to 500 subdomains. Proactively monitor incidents, data exposure risks and prevent Subdomain takeover attacks.
Get 14-day FREE with Asset Monitoring when sign up for a product DEMO.